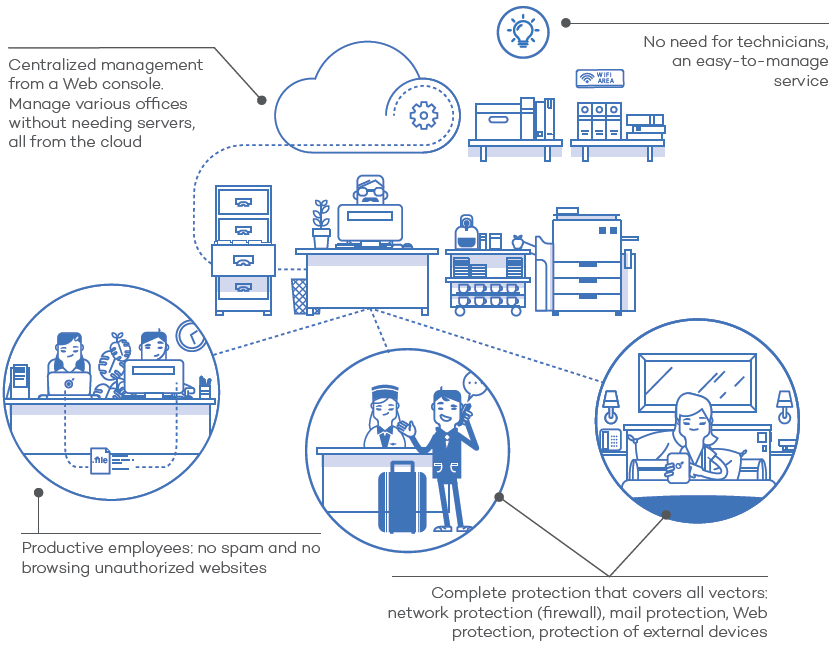
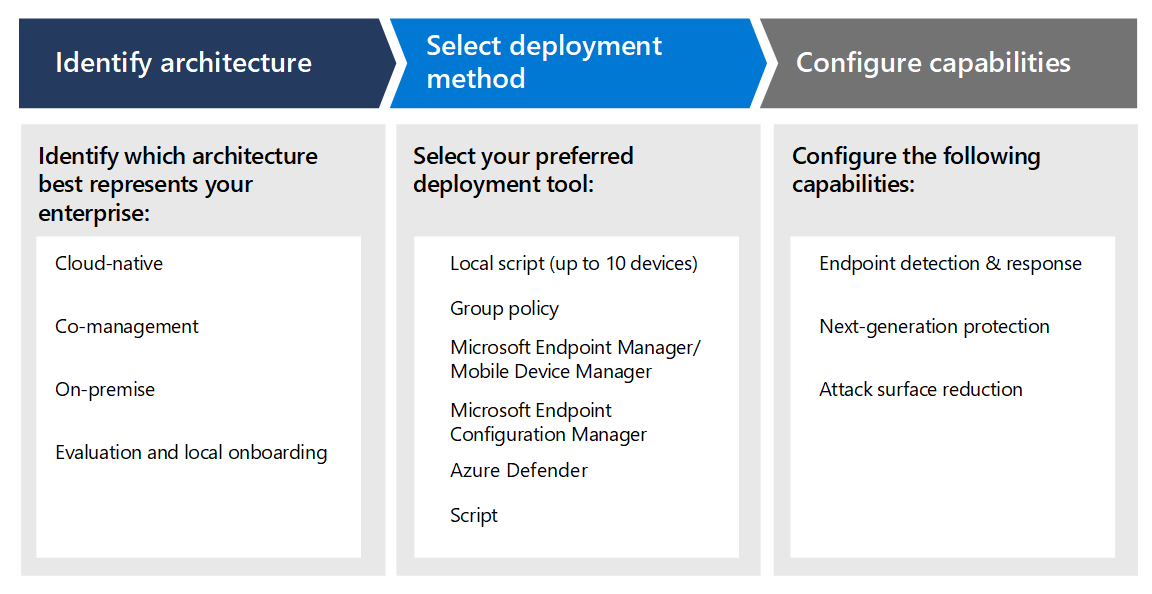
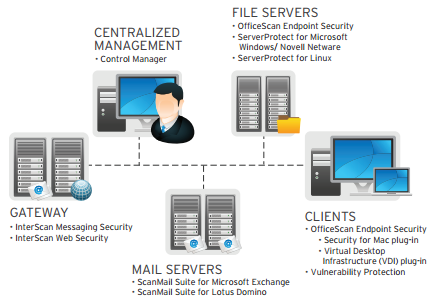
CrowdStrike Falcon Continues Impressive Record with Highest AAA Rating in SE Labs Enterprise Endpoint Protection Report | crowdstrike.com

Trend Micro Enterprise Security f/Endpoints Light v10.x, GOV, RNW, 251-500u, 32m, ML Government (GOV) Renewal Multilingual
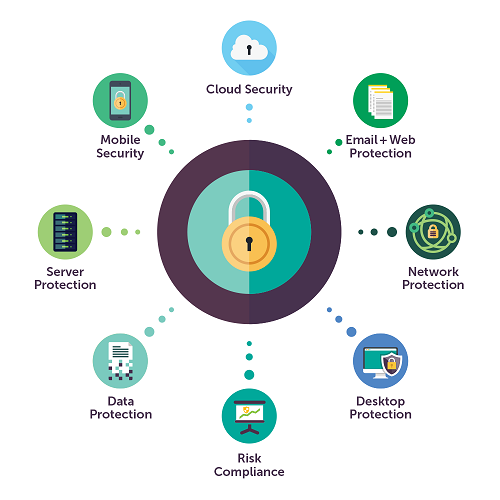
Enterprise Endpoint Security – Rules to Protect from Advanced Malware and Security Breaches – Xorlogics