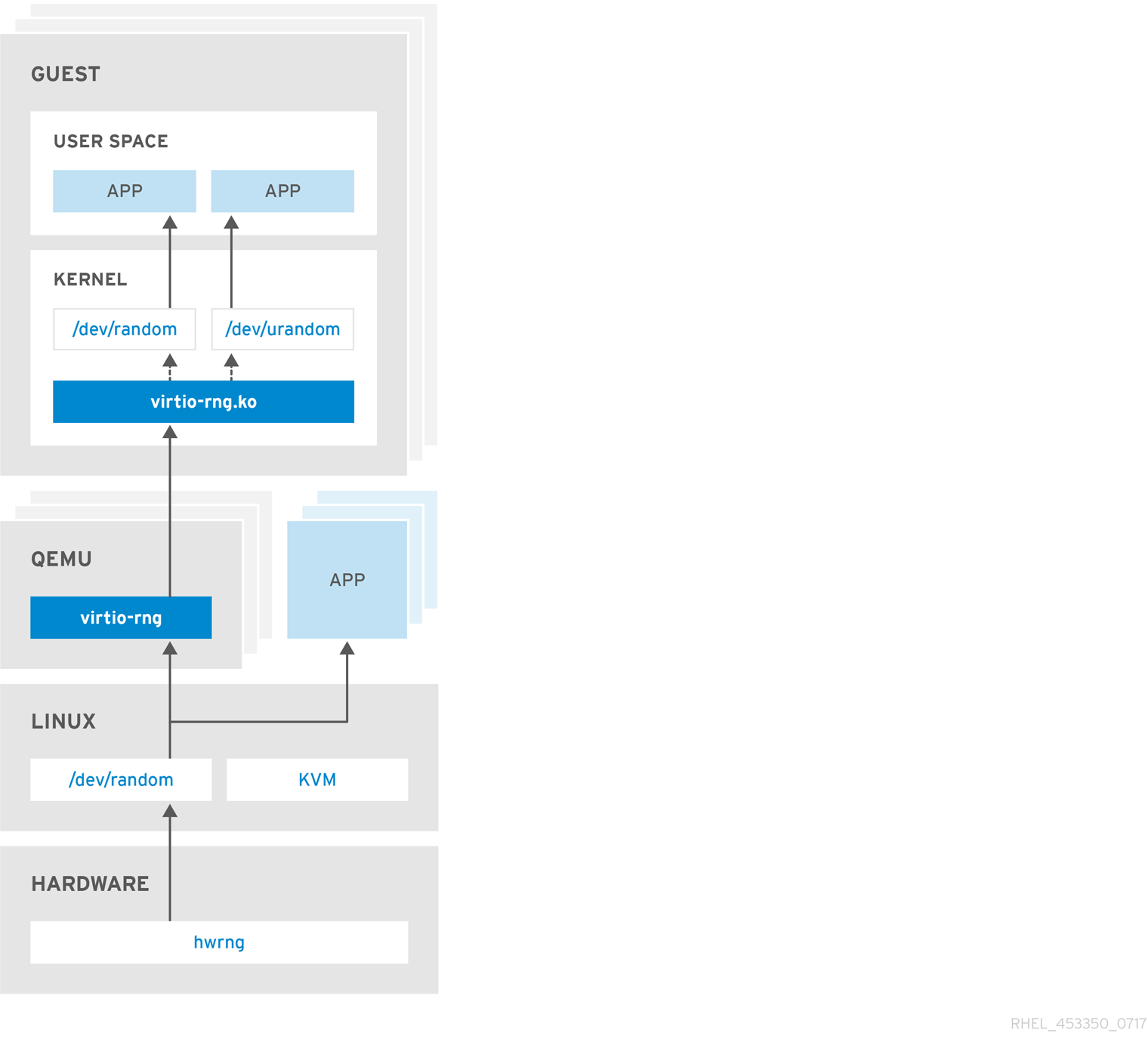
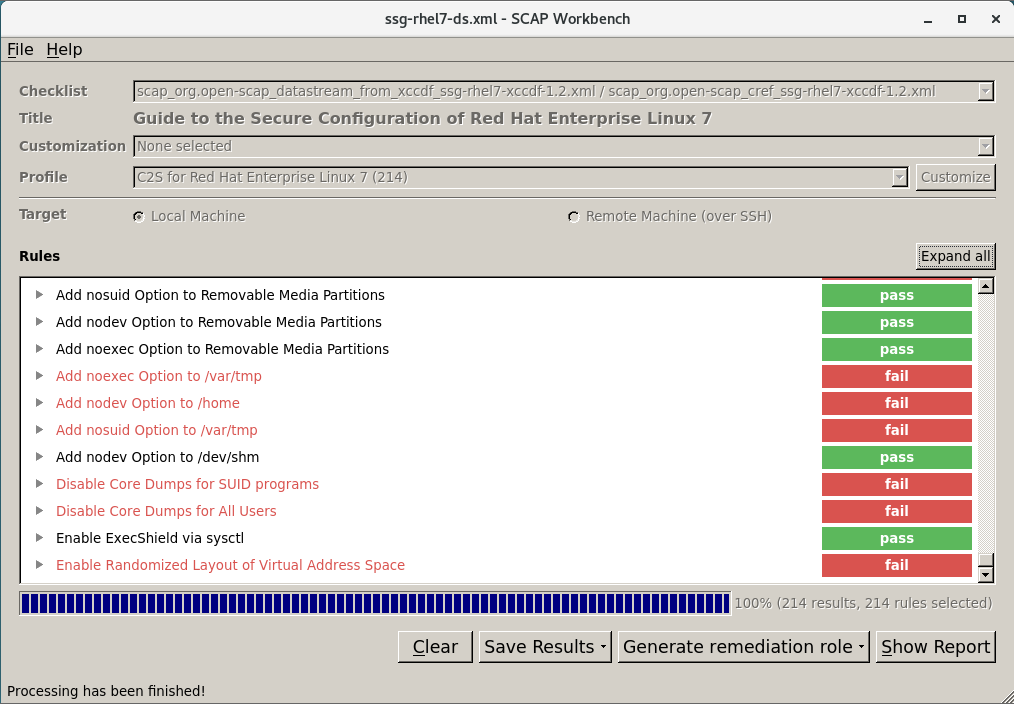
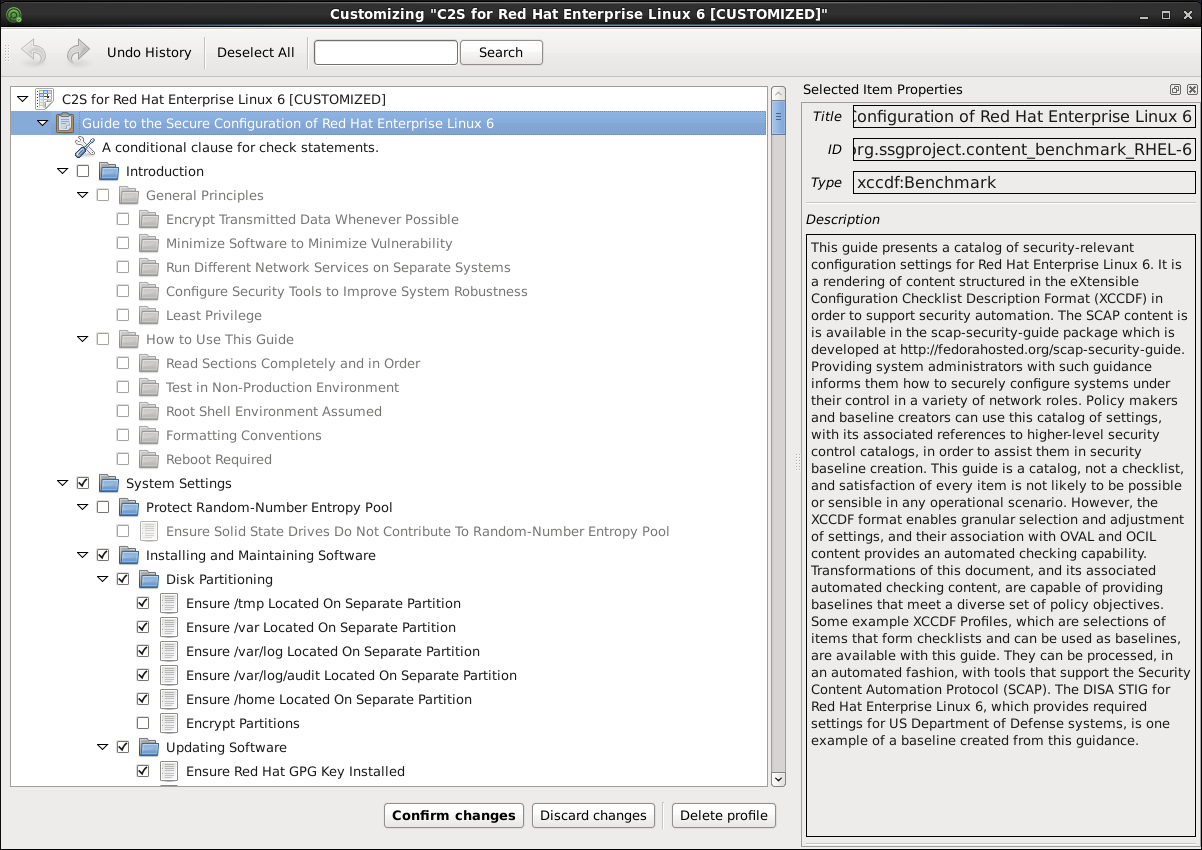
NSA Guide To The Secure Configuration of Red Hat Enterprise Linux 5: National Security Administration: 9781934302613: Amazon.com: Books

Red Hat Enterprise Linux 5: Administration Security Desktop: Petersen, Richard L: 9780982099803: Amazon.com: Books

Red Hat Enterprise Linux 8.3 delivers new security profiles and enhanced performance - Help Net Security

Learn Red Hat Linux Security: Includes Red Hat Linux 6.0: Doss, George M.: 9781556227738: Amazon.com: Books