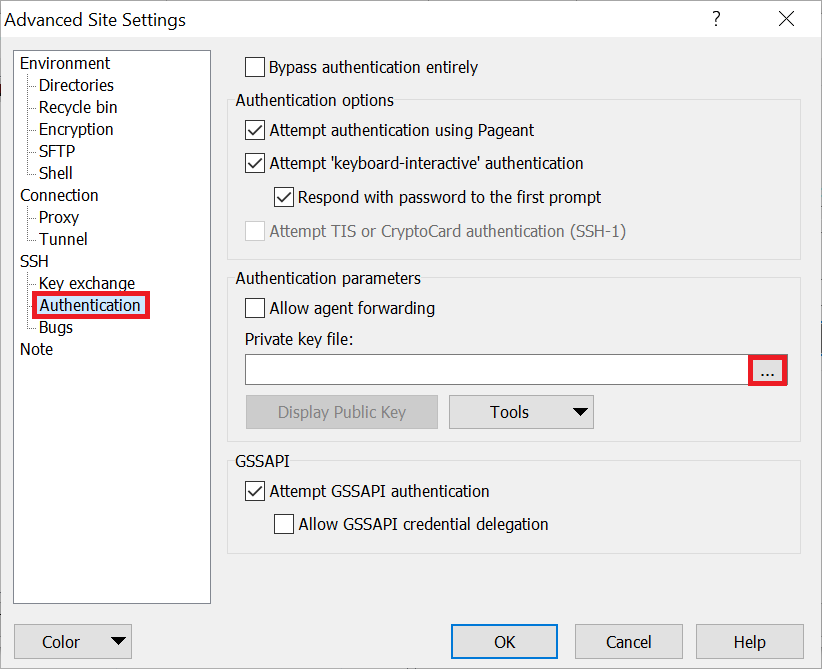
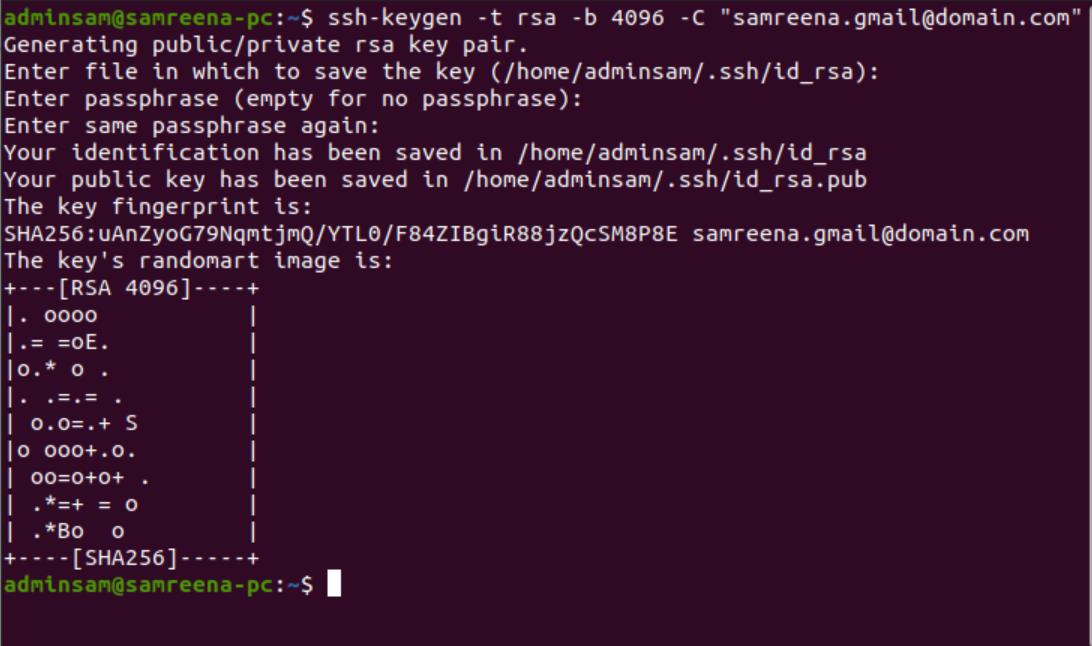
How To Configure SSH Key-Based Authentication on a Linux Server - Quality, Affordable Web Hosting & Dedicated Servers

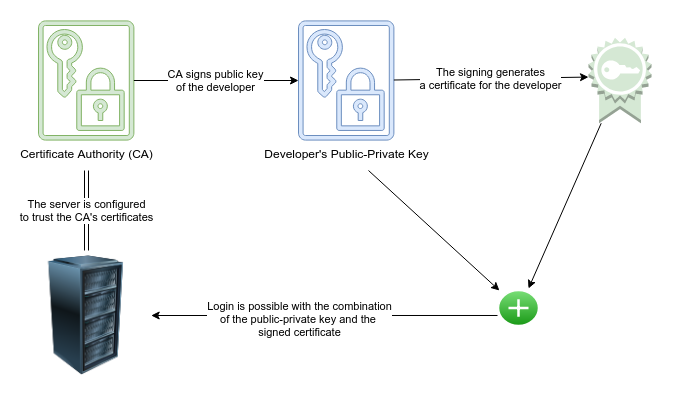
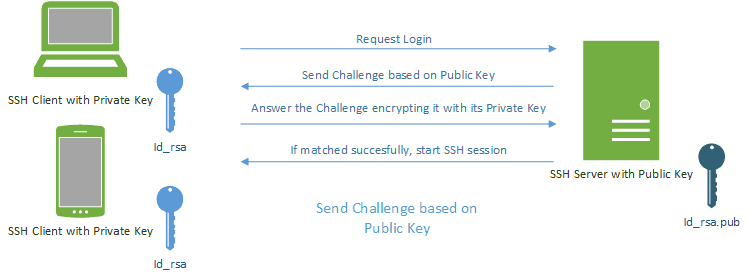
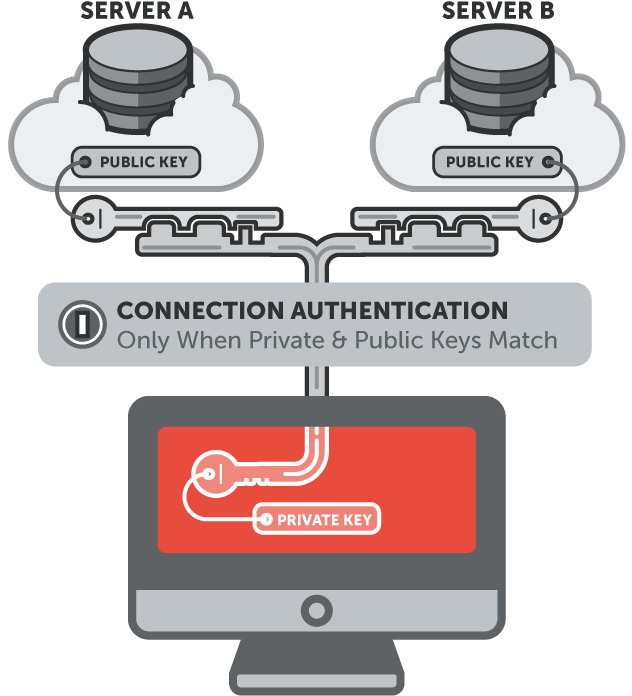
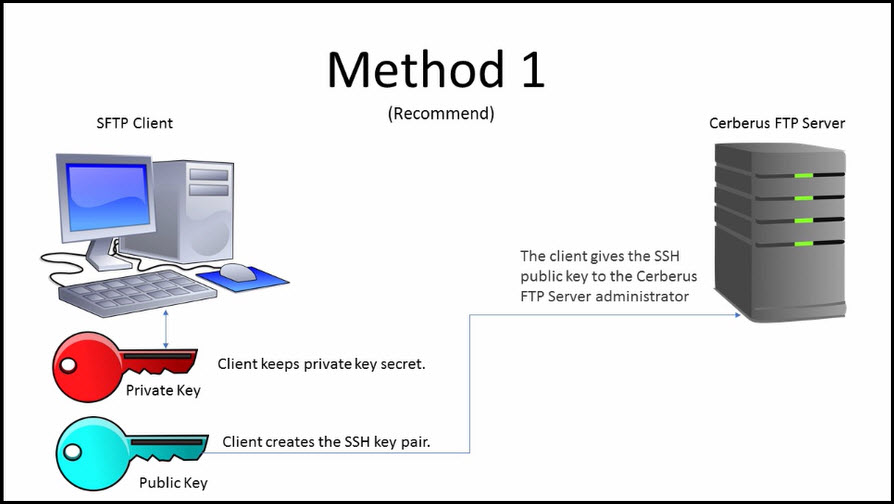
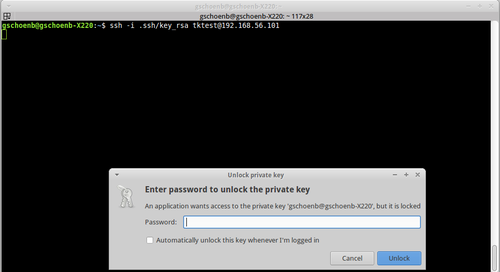
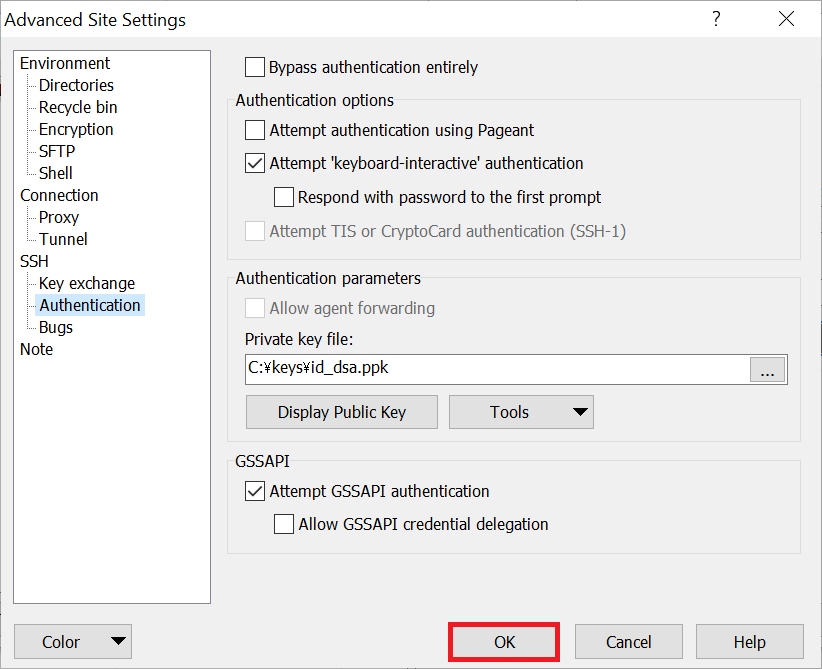
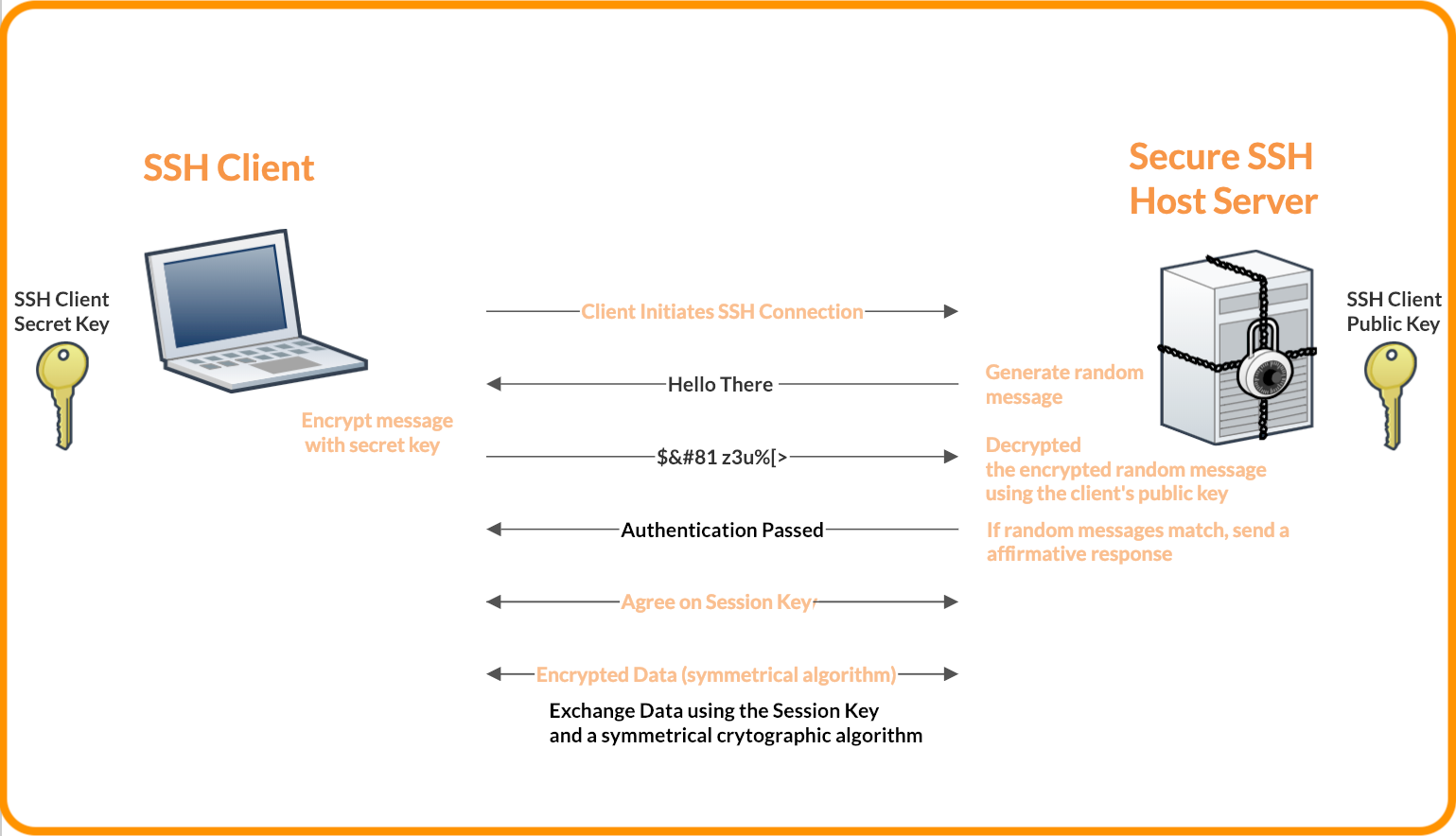
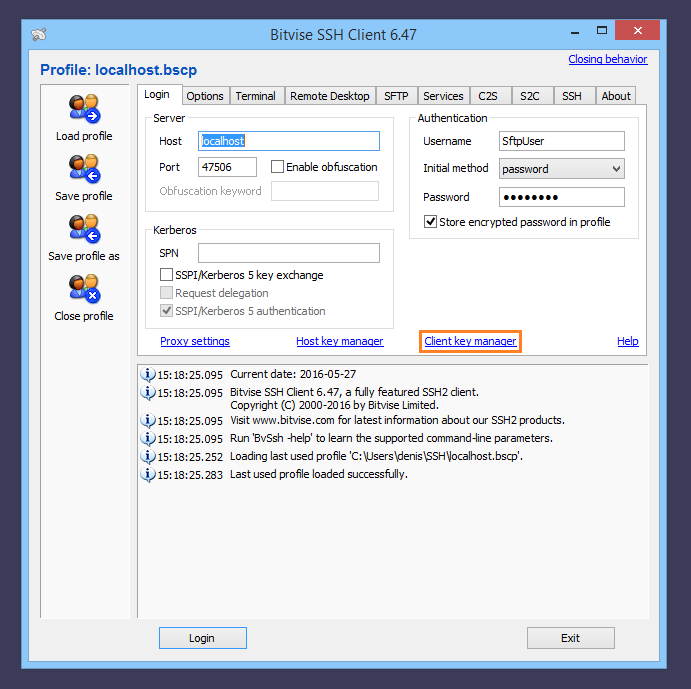
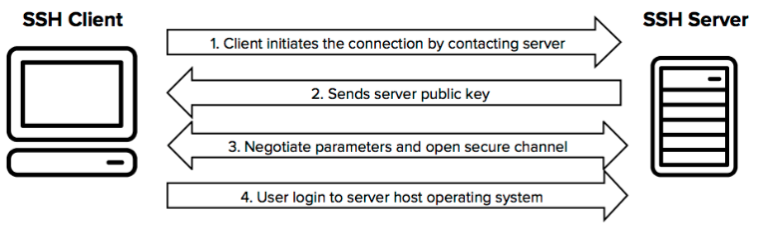
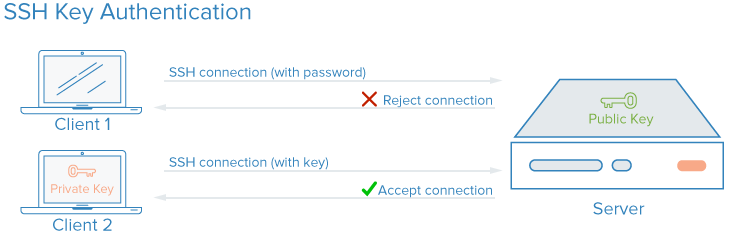
SSH keys authenticate users and hosts in SSH. They are used for single sign-on and machine-to-machine access. Security and convenience!